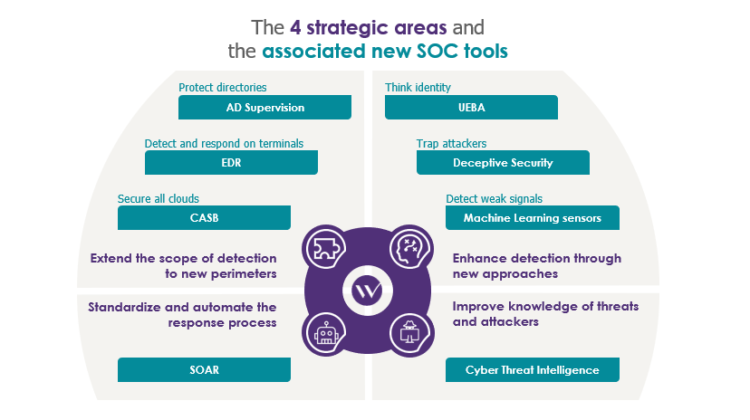
One feature-rich security technology that can monitor, manage, and react to security events and actions is the Security Orchestration, Automation, and Response architecture. It is also capable of organizing and automating these tasks. Security Orchestration, Automation, and Response, or SOAR, is the term for it. Thanks to SOAR’s various advantages, businesses may detect, assess, look into, deal with, and report hazards with ease. There’s a lot more things you excel at than this. By reducing the quantity of work that must be done by hand, cybersecurity professionals may be able to increase productivity and decrease response times.
An automated and standardized method of managing security activities is provided by SOAR cybersecurity. This shortens the time it takes for businesses to identify threats, safeguard their digital assets, and resolve security issues.
Assemble Information
By being more watchful, an organization may be able to strengthen its cyber security since SOAR continuously gathers and evaluates data. Smaller companies and sectors of the economy can also employ this strategy. It goes beyond the software that large corporations utilize to protect sensitive information from hackers and malfunctioning systems. It ought to benefit them. Using this in conjunction with routine backups to the cloud or additional hard drives could increase system security. No matter how big or little the company is, this is always the case.
Businesses may be able to identify specific security problems and find solutions with the aid of SOAR’s potent analytics, which would enhance the company’s overall security. Businesses looking for a more comprehensive method of defending their digital assets from potentially harmful attacks might consider the SOAR system.
Teams might learn topics more quickly, comprehend current events better, and take action with the aid of SOAR cybersecurity. Giving specifics regarding more complex aggressive behavior accomplishes this. Teams may now combine and automate operations that were previously completed by hand on a variety of platforms, all thanks to SOAR. Collecting, assessing, and addressing security-related issues are a few of these actions.
By enlightening companies about the entire assault chain, SOAR could improve their understanding of the environment in which they operate. A company or organization should speak with Blueshift Cybersecurity as soon as possible to receive guidance on how to set up SOAR if they want to be one step ahead of potential assaults. One solution is Blueshift Cybersecurity. One of the most well-known brands in the industry, Blueshift Cybersecurity, is dedicated to offering the highest caliber of internet security. Their plans don’t end with the launch of SOAR and SOC.
Examining the Functions of SOC
In the context of “Security Orchestration, Automation, and Response,” “SOAR” stands for. It is a crucial component of any effectively functioning Security Operations Center (SOC). With the use of SOAR technology, firms may streamline their security operations by eliminating manual labor-intensive procedures and managing regular chores. Companies may be able to devote less time and resources to security as a result. Making the process such that people are not required to participate helps achieve this. Employees at the Security Operations Center (SOC) can identify threats and develop effective response plans fast because of SOAR cybersecurity.
Data is sent to SOAR from many various sources, and SOAR analyzes it to provide SOC teams with actionable intelligence and assist them in determining the origin of an attack. Playbooks, which are documents that manage response activities like configuring firewall rules or obstructing harmful websites, can also be created using SOAR. These playbooks are located under the “Playbooks” tab if you’re using SOAR. It takes far less time for SOAR to detect dangers and respond to its environment because it is self-sufficient. This adjustment gives the security operations center employees more time to devise plans that would shield the business from potential threats. Thanks to a helpful technique called SOAR, increasing exposure is now not only feasible but also quite simple. Reaction times could be accelerated and SOC jobs made simpler with this technique. Any business that wishes to defend itself against threats must purchase SOAR.
Why It’s a Good Idea to Use SOAR in SOC
The fact that SOAR simplifies security responsibilities is among its most evident advantages when used in a SOC. The amount of effort required to complete difficult, time-consuming tasks that required human input can now be completed automatically without human input thanks to the modifications made to SOAR. This means that far less costly human resources are required in their place. Security operations centers, or SOCs, become more productive and have more resources available to them so they may concentrate on more critical duties, such as identifying threats and handling incidents.
Furthermore, SOAR improves analytical skills, which enables security personnel to identify potential threats more precisely and take prompt action. SOCs can now search through massive volumes of data using modern tools to uncover hidden patterns that were difficult, if not impossible, to uncover with more antiquated techniques. The SOAR program makes this function usable presently. People are more adept at handling issues because they are able to identify potential risks more quickly. IT professionals and company owners may concentrate on other duties when they are aware that their documents are secured against cyberattacks, accelerated online, and shielded by automatic protection. We can establish targets since modern technology manages the entire process. Before, this was not feasible.
Considering Your Priorities
Additionally, SOAR might significantly reduce false hits and simplify work organization for security personnel. Alerts may be more accurate and assist security operations centers (SOCs) in distinguishing between genuine threats and false alarms when paired with other security measures. Because they have more time to focus on other crucial tasks, people are less likely to overlook potentially dangerous circumstances.
Additionally, SOAR might greatly reduce the number of false warnings and assist security personnel in setting priorities. Security operations centers may be able to distinguish between genuine threats and false alarms more accurately when they combine SOAR with other technologies, thereby improving the accuracy of alerts. People are less likely to overlook items that could be harmful to their health as a result, and they have more time for other crucial tasks. Blueshift Cybersecurity is prepared to put an end to it if something similar should occur!
You can get in touch with the employees of Blueshift Security, an American organization, day or night. They continue to provide the managed protection services, SOAR systems, and products even after you leave for the day or return home at night. All alerts are under the control of Blueshift Cybersecurity, which will contact you if any suspicious activity is discovered. They will also provide you with details about previous procedures.
Additionally, Blueshift Cybersecurity will notify you if any safety precautions are implemented. You won’t have to worry about whether the resources and equipment you utilize are safe, which makes your job easier. Instead, you may concentrate on managing your company. With Blueshift Cybersecurity, you can be sure that your network is secure since they will take every precaution to maintain it that way. We may be found at www.blueshiftcyber.com; if this sounds like something you might be interested in, please get more information there.

Leave a Reply